Nothing is safe these days. It’s entirely reasonable if you’re anxious about security. There is an alarming increase in the number of security violations. One of the primary sources of concern is server security. Choosing a dedicated server hosting that provides services such as DDoS protection, firewalls, and other choices might help you better deal with these concerns.
Here is a list of the top dedicated server security recommendations:
- A strong password technique.
- Testing and analysis should be done on a regular basis.
- Firewall security.
- Keep the database up to date.
- Update the program on a regular basis.
- Backups of data.
- Professional Assist.
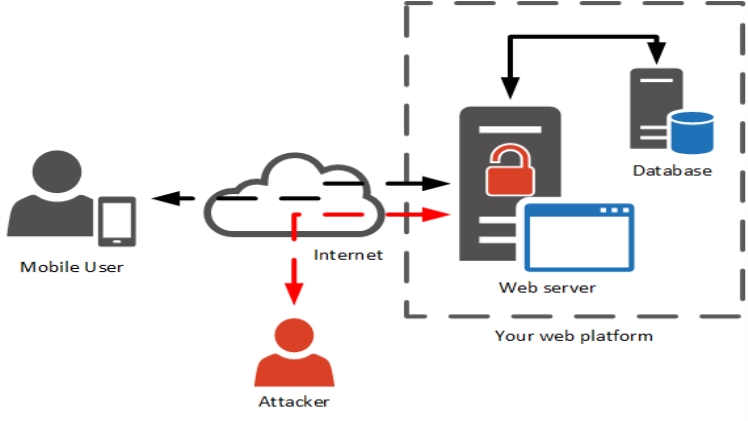
Password violation
The main reasons why so many businesses choose dedicated server hosting are high security and control. However, hackers can still get access to the hosting account and use more sophisticated techniques to corrupt or delete the data.
1. Strict password policy implementation
When you buy a new dedicated server, you should change the passwords. This is due to the fact that your host might provide a default password, increasing the likelihood of vulnerabilities.
The following procedures should be put in place for companies to protect the password:
- Use a random mix of upper and lowercase characters, numbers, and symbols.
- Avoid using phrases that are associated with your own identity.
- Do not store a password for an extended period of time.
Malware risk
Because it is simple to install a program on dedicated servers, the danger of infection is often considerable. Malware has the ability to copy your most sensitive and secret databases. They can be utilized with the programs and programs permitted.
2. Testing and analysis should be done on a regular basis.
- Look for a hosting company that provides regular vulnerability screening.
- Examine your website for any unusual behavior.
- Before posting to your website, test any applications on a safe, isolated home device.
DOS attack
By flooding the system with traffic, a DoS attack causes server failure and unavailability.
DDoS assaults are one sort of DoS attack in which numerous hostile computers collaborate to waste your hardware resources, overload your server with traffic, and harm genuine customers’ experiences.
3. Opt for a firewall
- Choose a dedicated server with the greatest hardware and ample system resources.
- Choose a hosting company that provides a high-quality perimeter firewall to prevent harmful data from reaching your server.
Website security
Intruders can exploit security flaws on your systems and thereby misappropriate personal and sensitive data.
4. Maintain your databases
The significance of data maintenance and upgrading cannot be overstated. Ascertain that your database is safe from SQL injection.
It is especially critical when gathering sensitive consumer information.
Other than that, you should look for:
- Reduce database users’ privileges.
- Delete any unnecessary data.
- When not required, avoid regions of contact between clients and the database.
5. Update the software regularly
Is your software out of date? That is the most serious error you are making right now.
Using obsolete software may result in a lack of security updates, patches, and other safeguards to keep your data safe.
- Install the latest version of the program whenever it becomes the available dedicated server.
- Use a reliable dedicated server security scan to stay up-to-date and protected.
6. Backups of data
You may be aware of the need of having a backup of your data following the WannaCry Ransomware and Petya attacks.
- Set up frequent backups of your data. Save vital data as a backup somewhere else so that in the case of an attack, you may retrieve it rather than losing it.
- Create a data restoration strategy in case the hard disk dies or external data is corrupted.
Off-site backups
Off-site backups are equally critical as on-site backups. Here are some things to think about:
- The site needs to be safe physically.
- It should be a reasonable distance from the initial backup location.
- It must be open to the public and verified.
7. Get proficient help
If you lack the necessary time and skills, jeopardizing the security of your dedicated server might cost you thousands of dollars. Contact us and we will send one of our skilled and certified personnel to take care of the following:
- Keep track of both basic and complicated web server designs.
- Identify vulnerabilities or malware that have been put into your server.
- Determine and prioritize security risks by identifying and reviewing vulnerabilities.

